1: History and Motivation
Examine the evolution of virtualization technologies from bare metal, virtual machines, and containers and the tradeoffs between them.
2: Technology Overview
Explores the three core Linux features that enable containers to function (cgroups, namespaces, and union filesystems), as well as the architecture of the Docker components.
3: Installation and Set Up
Install and configure Docker Desktop
4: Using 3rd Party Container Images
Use publicly available container images in your developer workflows and learn how about container data persistence.
5: Example Web Application
Building out a realistic microservice application to containerize.
6: Building Container Images
Write and optimize Dockerfiles and build container images for the components of the example web app.
7: Container Registries
Use container registries such as Dockerhub to share and distribute container images.
8: Running Containers
Use Docker and Docker Compose to run the containerized application from Module 5.
9: Container Security
Learn best practices for container image and container runtime security.
10: Interacting with Docker Objects
Explore how to use Docker to interact with containers, container images, volumes, and networks.
11: Development Workflow
Add tooling and configuration to enable improved developer experience when working with containers.
•Developer Experience Wishlist
12: Deploying Containers
Deploy containerized applications to production using a variety of approaches.

Linux Building Blocks
Containers leverage three linux features to work their magic:
- cgroups
- namespaces
- union fileystems
Cgroups and namespaces to provide resource constraints and application isolation respectively. They also use an union filesystem that enables images to be built upon common layers, making building and sharing images fast and efficient.
Note: Docker did not invent containers. For example, LXC containers (https://linuxcontainers.org/) was implemented in 2008, five years before Docker launched. That being said, Docker made huge strides in developer experience, which helped container technologies gain mass adoption and remains one the most popular containerization platforms.
Cgroups
Cgroups are a Linux kernel feature which allow processes to be organized into hierarchical groups whose usage of various types of resources can then be limited and monitored.
With cgroups, a container runtime is able to specify that a container should be able to use (for example):
- Use up to XX% of CPU cycles (cpu.shares)
- Use up to YY MB Memory (memory.limit_in_bytes)
- Throttle reads to ZZ MB/s (blkio.throttle.read_bps_device)
Namespaces
A namespace wraps a global system resource in an abstraction that makes it appear to the processes within the namespace that they have their own isolated instance of the global resource.
Changes to the global resource are visible to other processes that are members of the namespace, but are invisible to other processes.
With namespaces, a container runtime is able to keep processes outside of the container invisible within the container or map the user inside the container to a different user on the host (among other things).
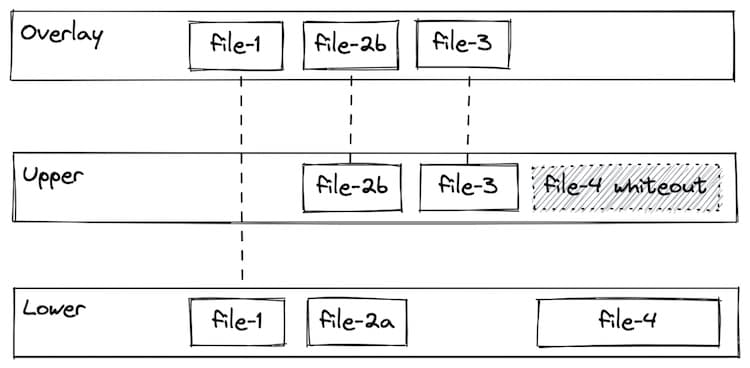
Union filesystems
A union filesystem allows files and directories of separate file systems, known as branches, to be transparently overlaid, forming a single coherent file system.
Contents of directories which have the same path within the merged branches will be seen together in a single merged directory, within the new, virtual filesystem.
This approach allows for efficient use of space because common layers can be shared. For example, if multiple containers from the same image are created on a single host, the container runtime only has to allocate a thin overlay specific to each container, while the underlying image layers can be shared. More detail on understanding the implications of these filesystem on data persistence can be found in 04-using-3rd-party-containers.
Docker provides a convenient user experience by packaging the underlying technologies (namespaces, cgroups, and union file systems) into an easy-to-use desktop application.
Additional Resources
For a deeper exploration of these topics, check out this awesome live stream by Joshua Jebaraj exploring cgroups and namespaces:
